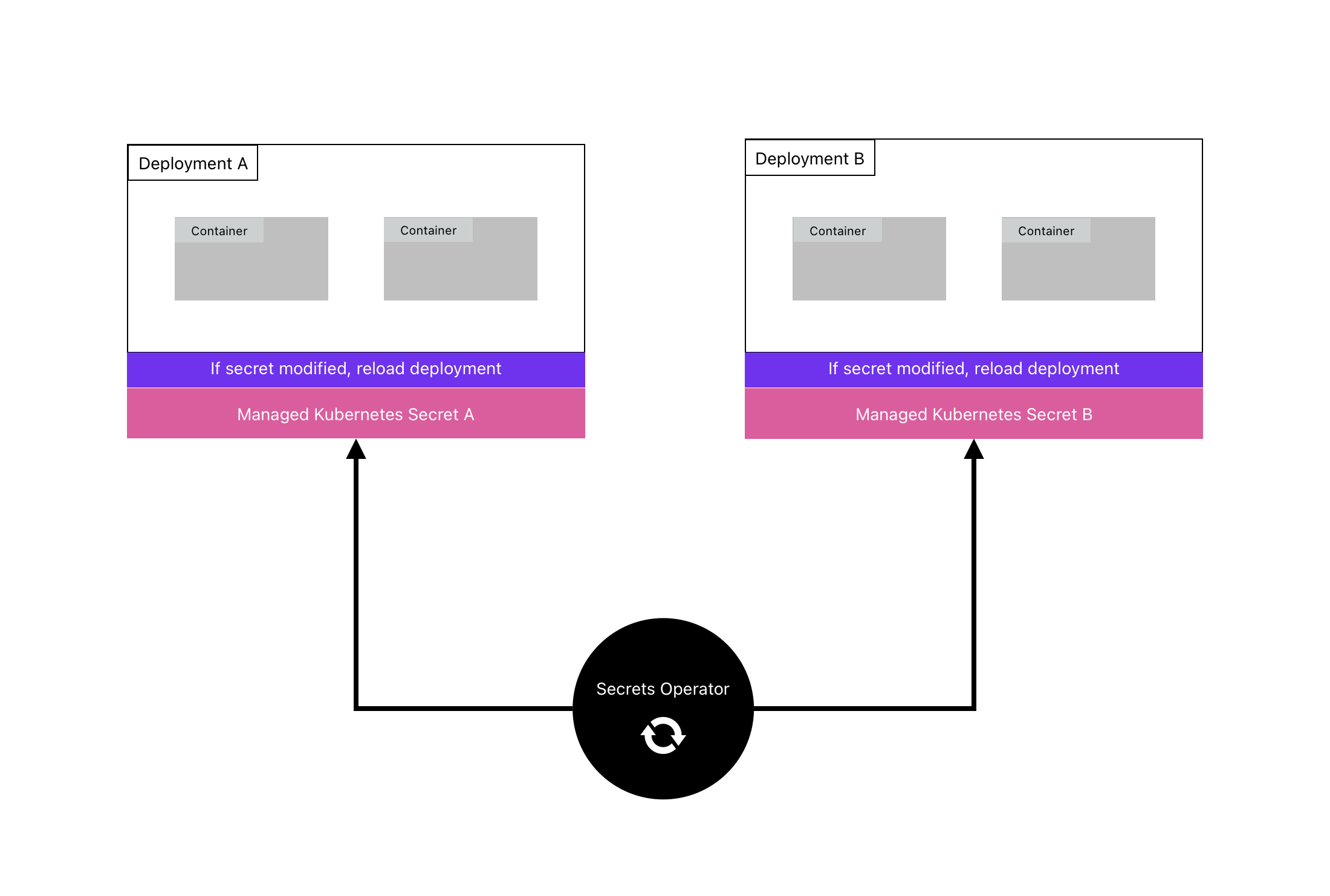
 The Infisical Secrets Operator is a Kubernetes controller that retrieves secrets from Infisical and stores them in a designated cluster.
It uses an
The Infisical Secrets Operator is a Kubernetes controller that retrieves secrets from Infisical and stores them in a designated cluster.
It uses an InfisicalSecret resource to specify authentication and storage methods.
The operator continuously updates secrets and can also reload dependent deployments automatically.
Install Operator
The operator can be install via Helm or kubectl- Helm (recommended)
- Kubectl
Install the latest Infisical Helm repositoryInstall the Helm chartFor production deployments, it is highly recommended to set the chart version and the application version during installs and upgrades.
This will prevent the operator from being accidentally updated to the latest version and introduce unintended breaking changes.View application versions here and chart versions here
Sync Infisical Secrets to your cluster
Once you have installed the operator to your cluster, you’ll need to create aInfisicalSecret custom resource definition (CRD).
example-infisical-secret-crd.yaml
InfisicalSecret CRD properties
hostAPI
hostAPI
If you are fetching secrets from a self hosted instance of Infisical set the value of
hostAPI to
https://your-self-hosted-instace.com/apiWhen hostAPI is not defined the operator fetches secrets from Infisical Cloud.Advanced use case
Advanced use case
If you have installed your Infisical instance within the same cluster as the Infisical operator, you can optionally access the Infisical backend’s service directly without having to route through the public internet.
To achieve this, use the following address for the hostAPI field:Make sure to replace
<backend-svc-name> and <namespace> with the appropriate values for your backend service and namespace.resyncInterval
resyncInterval
This property defines the time in seconds between each secret re-sync from Infisical. Shorter time between re-syncs will require higher rate limits only available on paid plans.
Default re-sync interval is every 1 minute.
authentication
authentication
This block defines the method that will be used to authenticate with Infisical so that secrets can be fetched
authentication.universalAuth
authentication.universalAuth
The universal machine identity authentication method is used to authenticate with Infisical. The client ID and client secret needs to be stored in a Kubernetes secret. This block defines the reference to the name and namespace of secret that stores these credentials.
Create a machine identity
You need to create a machine identity, and give it access to the project(s) you want to interact with. You can read more about machine identities here.
Create Kubernetes secret containing machine identity credentials
Once you have created your machine identity and added it to your project(s), you will need to create a Kubernetes secret containing the identity credentials.
To quickly create a Kubernetes secret containing the identity credentials, you can run the command below.Make sure you replace
<your-identity-client-id> with the identity client ID and <your-identity-client-secret> with the identity client secret.Make sure to also populate the
secretsScope field with the project slug projectSlug, environment slug envSlug, and secrets path secretsPath that you want to fetch secrets from. Please see the example below.Example
authentication.serviceToken
authentication.serviceToken
The service token required to authenticate with Infisical needs to be stored in a Kubernetes secret. This block defines the reference to the name and namespace of secret that stores this service token.
Follow the instructions below to create and store the service token in a Kubernetes secrets and reference it in your CRD.
1. Generate service token
You can generate a service token for an Infisical project by heading over to the Infisical dashboard then to Project Settings.2. Create Kubernetes secret containing service token
Once you have generated the service token, you will need to create a Kubernetes secret containing the service token you generated. To quickly create a Kubernetes secret containing the generated service token, you can run the command below. Make sure you replace<your-service-token-here> with your service token.3. Add reference for the Kubernetes secret containing service token
Once the secret is created, add the name and namespace of the secret that was just created underauthentication.serviceToken.serviceTokenSecretReference field in the InfisicalSecret resource.Make sure to also populate the
secretsScope field with the, environment slug envSlug, and secrets path secretsPath that you want to fetch secrets from. Please see the example below.Example
managedSecretReference
managedSecretReference
The
managedSecretReference field is used to define the target location for storing secrets retrieved from an Infisical project.
This field requires specifying both the name and namespace of the Kubernetes secret that will hold these secrets.
The Infisical operator will automatically create the Kubernetes secret with the specified name/namespace and keep it continuously updated.Note: The managed secret be should be created in the same namespace as the deployment that will use it.managedSecretReference.secretName
managedSecretReference.secretName
The name of the managed Kubernetes secret to be created
managedSecretReference.secretNamespace
managedSecretReference.secretNamespace
The namespace of the managed Kubernetes secret to be created.
managedSecretReference.secretType
managedSecretReference.secretType
Override the default Opaque type for managed secrets with this field. Useful for creating kubernetes.io/dockerconfigjson secrets.
managedSecretReference.creationPolicy
managedSecretReference.creationPolicy
Creation polices allow you to control whether or not owner references should be added to the managed Kubernetes secret that is generated by the Infisical operator.
This is useful for tools such as ArgoCD, where every resource requires an owner reference; otherwise, it will be pruned automatically.
Available options
Orphan(default)Owner
Propagating labels & annotations
The operator will transfer all labels & annotations present on theInfisicalSecret CRD to the managed Kubernetes secret to be created.
Thus, if a specific label is required on the resulting secret, it can be applied as demonstrated in the following example:
Example propagation
Example propagation
Apply the Infisical CRD to your cluster
Once you have configured the Infisical CRD with the required fields, you can apply it to your cluster. After applying, you should notice that the managed secret has been created in the desired namespace your specified.Verify managed secret creation
To verify that the operator has successfully created the managed secret, you can check the secrets in the namespace that was specified.The Infisical secrets will be synced and stored into the managed secret every
1 minutes.
Using managed secret in your deployment
Incorporating the managed secret created by the operator into your deployment can be achieved through several methods. Here, we will highlight three of the most common ways to utilize it. Learn more about Kubernetes secrets hereenvFrom
envFrom
This will take all the secrets from your managed secret and expose them to your containerExample usage in a deployment
env
env
This will allow you to select individual secrets by key name from your managed secret and expose them to your containerExample usage in a deployment
volumes
volumes
This will allow you to create a volume on your container which comprises of files holding the secrets in your managed kubernetes secretYou can then mount this volume to the container’s filesystem so that your deployment can access the files containing the managed secretsExample usage in a deployment
Auto redeployment
Deployments using managed secrets don’t reload automatically on updates, so they may use outdated secrets unless manually redeployed. To address this, we added functionality to automatically redeploy your deployment when its managed secret updates.Enabling auto redeploy
To enable auto redeployment you simply have to add the following annotation to the deployment that consumes a managed secretDeployment example with auto redeploy enabled
Deployment example with auto redeploy enabled
Global configuration
To configure global settings that will apply to all instances ofInfisicalSecret, you can define these configurations in a Kubernetes ConfigMap.
For example, you can configure all InfisicalSecret instances to fetch secrets from a single backend API without specifying the hostAPI parameter for each instance.
Available global properties
| Property | Description | Default value |
|---|---|---|
| hostAPI | If hostAPI in InfisicalSecret instance is left empty, this value will be used | https://app.infisical.com/api |
Applying global configurations
All global configurations must reside in a Kubernetes ConfigMap namedinfisical-config in the namespace infisical-operator-system.
To apply global configuration to the operator, copy the following yaml into infisical-config.yaml file.
infisical-config.yaml
Troubleshoot operator
If the operator is unable to fetch secrets from the API, it will not affect the managed Kubernetes secret. It will continue attempting to reconnect to the API indefinitely. The InfisicalSecret resource uses thestatus.conditions field to report its current state and any errors encountered.
Uninstall Operator
The managed secret created by the operator will not be deleted when the operator is uninstalled.- Helm
- Kubectl
Install Infisical Helm repository

