Key features:
- Token renewal: Automatically authenticates with Infisical and deposits renewed access tokens at specified path for applications to consume
- Templating: Renders secrets via user provided templates to desired formats for applications to consume
Token renewal
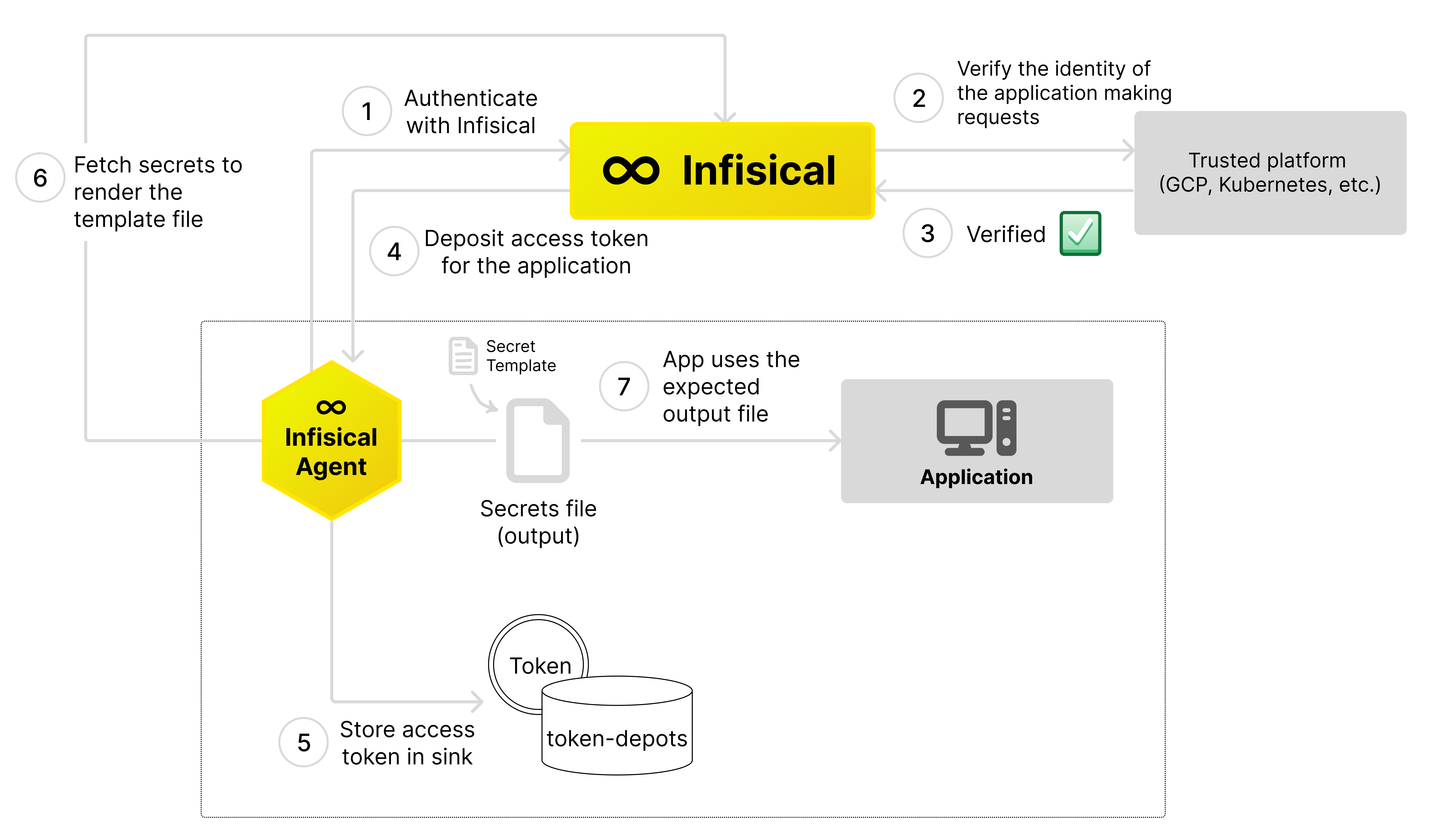
The Infisical agent can help manage the life cycle of access tokens. The token renewal process is split into two main components: aMethod, which is the authentication process suitable for your current setup, and Sinks, which are the places where the agent deposits the new access token whenever it receives updates.
When the Infisical Agent is started, it will attempt to obtain a valid access token using the authentication method you have configured. If the agent is unable to fetch a valid token, the agent will keep trying, increasing the time between each attempt.
Once a access token is successfully fetched, the agent will make sure the access token stays valid, continuing to renew it before it expires.
Every time the agent successfully retrieves a new access token, it writes the new token to the Sinks you’ve configured.
Access tokens can be utilized with Infisical SDKs or directly in API requests to retrieve secrets from Infisical
Templating
The Infisical agent can help deliver formatted secrets to your application in a variety of environments. To achieve this, the agent will retrieve secrets from Infisical, format them using a specified template, and then save these formatted secrets to a designated file path. Templating process is done through the use of Go language’s text/template feature. Multiple template definitions can be set in the agent configuration file to generate a variety of formatted secret files. When the agent is started and templates are defined in the agent configuration file, the agent will attempt to acquire a valid access token using the set authentication method outlined in the agent’s configuration. If this initial attempt is unsuccessful, the agent will momentarily pauses before continuing to make more attempts. Once the agent successfully obtains a valid access token, the agent proceeds to fetch the secrets from Infisical using it. It then formats these secrets using the user provided templates and writes the formatted data to configured file paths.Agent configuration file
To set up the authentication method for token renewal and to define secret templates, the Infisical agent requires a YAML configuration file containing properties defined below. While specifying an authentication method is mandatory to start the agent, configuring sinks and secret templates are optional.| Field | Description |
|---|---|
infisical.address | The URL of the Infisical service. Default: "https://app.infisical.com". |
auth.type | The type of authentication method used. Only "universal-auth" type is currently available |
auth.config.client-id | The file path where the universal-auth client id is stored. |
auth.config.client-secret | The file path where the universal-auth client secret is stored. |
auth.config.remove_client_secret_on_read | This will instruct the agent to remove the client secret from disk. |
sinks[].type | The type of sink in a list of sinks. Each item specifies a sink type. Currently, only "file" type is available. |
sinks[].config.path | The file path where the access token should be stored for each sink in the list. |
templates[].source-path | The path to the template file that should be used to render secrets. |
templates[].destination-path | The path where the rendered secrets from the source template will be saved to. |
templates[].config.polling-interval | How frequently to check for secret changes. Default: 5 minutes (optional) |
templates[].config.execute.command | The command to execute when secret change is detected (optional) |
templates[].config.execute.timeout | How long in seconds to wait for command to execute before timing out (optional) |
Quick start Infisical Agent
To install the Infisical agent, you must first install the Infisical CLI in the desired environment where you’d like the agent to run. This is because the Infisical agent is a sub-command of the Infisical CLI. Once you have the CLI installed, you will need to provision programmatic access for the agent via Universal Auth. To obtain a Client ID and a Client Secret, follow the step by step guide outlined here. Next, create agent config file as shown below.example-agent-config-file.yaml
my-dot-ev-secret-template
= sign. You’ll notice that a custom function named secret is used to fetch the secrets.
This function takes the following arguments: secret "<project-id>" "<environment-slug>" "<secret-path>".

